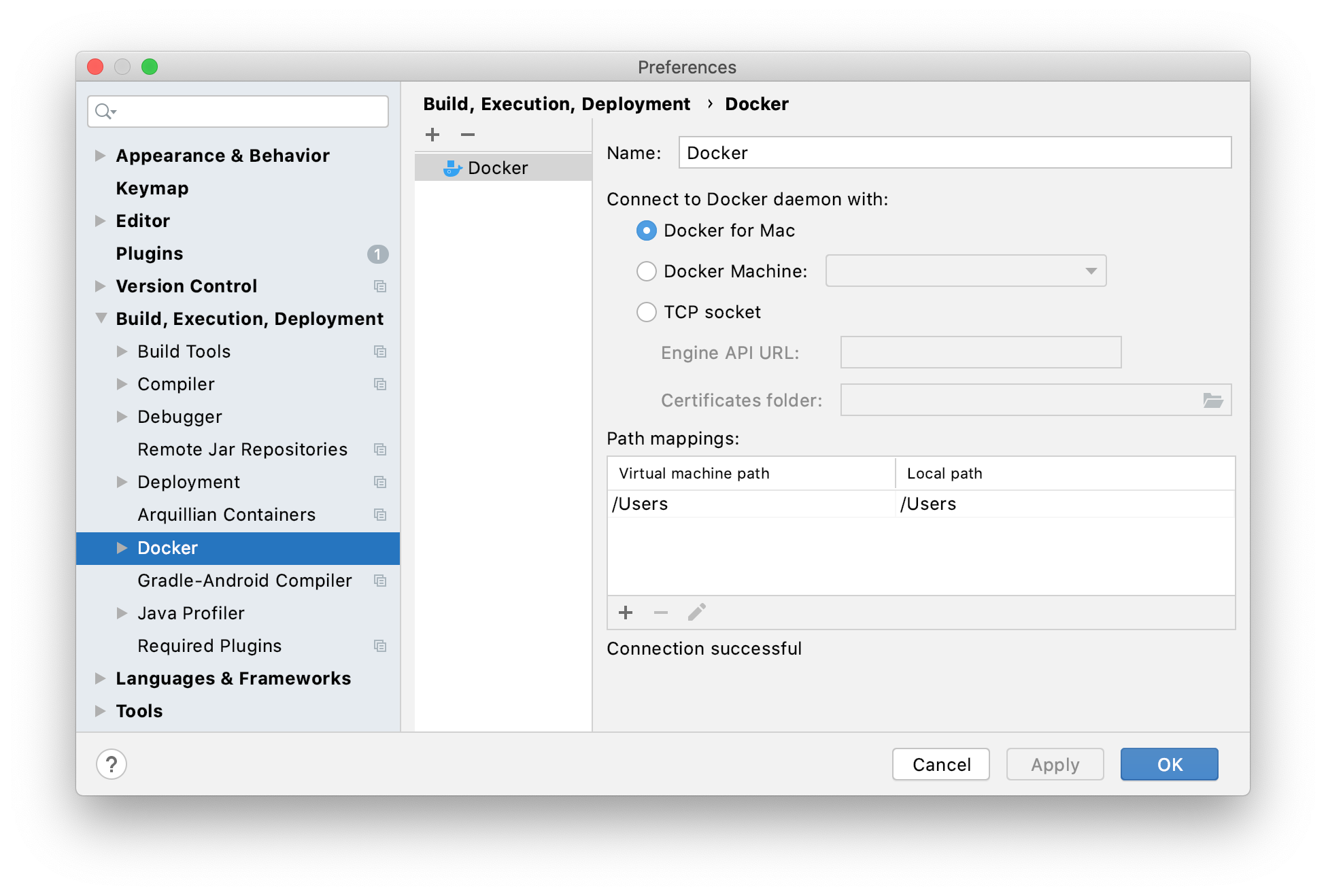
Macos Docker Install
- Installing
- macOS troubleshooting
Docker uses containers to create virtual environments that isolate a TensorFlow installation from the rest of the system. TensorFlow programs are run within this virtual environment that can share resources with its host machine (access directories, use the GPU, connect to the Internet, etc.). MacOS Code Signing works only on macOS. Cannot be fixed. Free public Electron Build Service is used to build Electron app for Linux on Windows. On macOS/Linux you can build Electron app for Windows locally, except Appx for Windows Store (in the future (feel free to file issue) electron-build-service will support Appx target).
GitLab Runner can be installed and updated on macOS.
Installing
There are two methods for installing GitLab Runner on macOS:
- Manual installation. This method is officially supported and recommended by GitLab.
- Homebrew installation. Install with Homebrew as an alternative to manual installation.
Manual installation (official)
Download the binary for your system:
You can download a binary for every available version as described inBleeding Edge - download any other tagged release.
Give it permissions to execute:
The rest of the commands should execute as the user who will run the runners.
- When you build iOS or macOS applications on macOS, use the shell executor.The build and tests run as the identity of the logged-in user, directly on the build host.It does not run in a container. This is less secure than using container executors. For more information, see thesecurity implications documentationfor additional detail on what to keep in mind in this scenario.
Install GitLab Runner as a service and start it:
GitLab Runner is installed and will be run after a system reboot.
Homebrew installation (alternative)
A Homebrew formula is available to install GitLab.
To install GitLab Runner using Homebrew:
Install GitLab Runner.
Install GitLab Runner as a service and start it.
GitLab Runner is installed and running.
Limitations on macOS
Currently, the only proven way for it to work in macOS is by running the service in user-mode.
Since the service will be running only when the user is logged in, you shouldenable auto-login on your macOS machine.
The service will be launched as a LaunchAgent. By using LaunchAgents,the builds will be able to perform UI interactions, making it possible to run andtest in the iOS simulator.
It’s worth noting that macOS also has LaunchDaemons, services runningcompletely in background. LaunchDaemons are run on system startup, but theydon’t have the same access to UI interactions as LaunchAgents. You can try torun the Runner’s service as a LaunchDaemon, but this mode of operation is notcurrently supported.
You can verify that GitLab Runner created the service configuration file afterexecuting the install command, by checking the~/Library/LaunchAgents/gitlab-runner.plist file.
If Homebrew was used to install git, it may have added a /usr/local/etc/gitconfig filecontaining:
This tells Git to cache user credentials in the keychain, which may not be what you wantand can cause fetches to hang. You can remove the line from the system gitconfigwith:
Alternatively, you can just disable credential.helper for the GitLab user:
You can check the status of the credential.helper with:
Manual update
Stop the service:
Download the binary to replace the GitLab Runner executable:
You can download a binary for every available version as described inBleeding Edge - download any other tagged release.
Give it permissions to execute:
Start the service:
Make sure that you read the FAQ section which describessome of the most common problems with GitLab Runner.
Upgrade the service file
In order to upgrade the LaunchAgent configuration, you need to uninstall andinstall the service:
Using codesign with the GitLab Runner Service
If you installed gitlab-runner on macOS with homebrew and your build callscodesign, you may need to set <key>SessionCreate</key><true/> to haveaccess to the user keychains. In the following example we run the builds as the gitlabuser and want access to the signing certificates installed by that user for codesigning:
macOS troubleshooting
The following relate to troubleshooting on macOS.
'launchctl' failed: exit status 112, Could not find domain for
This message may occur when you try to install GitLab Runner on macOS. Make surethat you manage GitLab Runner service from the GUI Terminal application, notthe SSH connection.
Failed to authorize rights (0x1) with status: -60007.
If GitLab Runner is stuck on the above message when using macOS, there are twocauses to why this happens:
Make sure that your user can perform UI interactions:
The first command enables access to developer tools for your user.The second command allows the user who is member of the developer group todo UI interactions, e.g., run the iOS simulator.
Make sure that your GitLab Runner service doesn’t use
SessionCreate = true.Previously, when running GitLab Runner as a service, we were creatingLaunchAgentswithSessionCreate. At that point (Mavericks), this wasthe only solution to make Code Signing work. That changed recently withOS X El Capitan which introduced a lot of new security features thataltered this behavior.Since GitLab Runner 1.1, when creating aLaunchAgent, we don’t setSessionCreate. However, in order to upgrade, you need to manuallyreinstall theLaunchAgentscript:Then you can verify that
~/Library/LaunchAgents/gitlab-runner.plisthasSessionCreateset tofalse.
fatal: unable to access 'https://path:3000/user/repo.git/': Failed to connect to path port 3000: Operation timed out error in the job
If one of the jobs fails with this error, make sure the runner can connect to your GitLab instance. The connection could be blocked by things like:
- firewalls
- proxies
- permissions
- routing configurations
Help & feedback
Docs
Edit this pageto fix an error or add an improvement in a merge request.Create an issueto suggest an improvement to this page.
Show and post commentsto review and give feedback about this page.
Product
Create an issueif there's something you don't like about this feature.Propose functionalityby submitting a feature request.
Join First Lookto help shape new features.
Feature availability and product trials
View pricingto see all GitLab tiers and features, or to upgrade.Try GitLab for freewith access to all features for 30 days.
Get Help
If you didn't find what you were looking for,search the docs.
If you want help with something specific and could use community support,post on the GitLab forum.
For problems setting up or using this feature (depending on your GitLabsubscription).
Elasticsearch is also available as Docker images.The images use centos:8 as the base image.
A list of all published Docker images and tags is available atwww.docker.elastic.co. The source filesare inGithub.
This package contains both free and subscription features.Start a 30-day trial to try out all of the features.
Obtaining Elasticsearch for Docker is as simple as issuing a docker pull commandagainst the Elastic Docker registry.
To start a single-node Elasticsearch cluster for development or testing, specifysingle-node discovery to bypass the bootstrap checks:
Starting a multi-node cluster with Docker Composeedit
To get a three-node Elasticsearch cluster up and running in Docker,you can use Docker Compose:
This sample docker-compose.yml file uses the ES_JAVA_OPTSenvironment variable to manually set the heap size to 512MB. We do not recommendusing ES_JAVA_OPTS in production. See Manually set the heap size.
This sample Docker Compose file brings up a three-node Elasticsearch cluster.Node es01 listens on localhost:9200 and es02 and es03 talk to es01 over a Docker network.
Please note that this configuration exposes port 9200 on all network interfaces, and given howDocker manipulates iptables on Linux, this means that your Elasticsearch cluster is publically accessible,potentially ignoring any firewall settings. If you don’t want to expose port 9200 and instead usea reverse proxy, replace 9200:9200 with 127.0.0.1:9200:9200 in the docker-compose.yml file.Elasticsearch will then only be accessible from the host machine itself.
The Docker named volumesdata01, data02, and data03 store the node data directories so the data persists across restarts.If they don’t already exist, docker-compose creates them when you bring up the cluster.
Make sure Docker Engine is allotted at least 4GiB of memory.In Docker Desktop, you configure resource usage on the Advanced tab in Preference (macOS)or Settings (Windows).
Docker Compose is not pre-installed with Docker on Linux.See docs.docker.com for installation instructions:Install Compose on Linux
Run
docker-composeto bring up the cluster:Submit a
_cat/nodesrequest to see that the nodes are up and running:
Log messages go to the console and are handled by the configured Docker logging driver.By default you can access logs with docker logs. If you would prefer the Elasticsearchcontainer to write logs to disk, set the ES_LOG_STYLE environment variable to file.This causes Elasticsearch to use the same logging configuration as other Elasticsearch distribution formats.

To stop the cluster, run docker-compose down.The data in the Docker volumes is preserved and loadedwhen you restart the cluster with docker-compose up.To delete the data volumes when you bring down the cluster,specify the -v option: docker-compose down -v.
See Encrypting communications in an Elasticsearch Docker Container andRun the Elastic Stack in Docker with TLS enabled.
The following requirements and recommendations apply when running Elasticsearch in Docker in production.
The vm.max_map_count kernel setting must be set to at least 262144 for production use.
How you set vm.max_map_count depends on your platform:
Linux
The
vm.max_map_countsetting should be set permanently in/etc/sysctl.conf:To apply the setting on a live system, run:
macOS with Docker for Mac
The
vm.max_map_countsetting must be set within the xhyve virtual machine:From the command line, run:
Press enter and use`sysctl` to configure
vm.max_map_count:- To exit the
screensession, typeCtrl a d.
Windows and macOS with Docker Desktop
The
vm.max_map_countsetting must be set via docker-machine:Windows with Docker Desktop WSL 2 backend
The
vm.max_map_countsetting must be set in the docker-desktop container:

Configuration files must be readable by the elasticsearch useredit
By default, Elasticsearch runs inside the container as user elasticsearch usinguid:gid 1000:0.
One exception is Openshift,which runs containers using an arbitrarily assigned user ID.Openshift presents persistent volumes with the gid set to 0, which works without any adjustments.
If you are bind-mounting a local directory or file, it must be readable by the elasticsearch user.In addition, this user must have write access to the config, data and log dirs(Elasticsearch needs write access to the config directory so that it can generate a keystore).A good strategy is to grant group access to gid 0 for the local directory.
For example, to prepare a local directory for storing data through a bind-mount:
You can also run an Elasticsearch container using both a custom UID and GID. Unless youbind-mount each of the config, data` and logs directories, you must passthe command line option --group-add 0 to docker run. This ensures that the userunder which Elasticsearch is running is also a member of the root (GID 0) group inside thecontainer.
As a last resort, you can force the container to mutate the ownership ofany bind-mounts used for the data and log dirs through theenvironment variable TAKE_FILE_OWNERSHIP. When you do this, they will be owned byuid:gid 1000:0, which provides the required read/write access to the Elasticsearch process.
Increased ulimits for nofile and nprocmust be available for the Elasticsearch containers.Verify the init systemfor the Docker daemon sets them to acceptable values.
To check the Docker daemon defaults for ulimits, run:
If needed, adjust them in the Daemon or override them per container.For example, when using docker run, set:
Swapping needs to be disabled for performance and node stability.For information about ways to do this, see Disable swapping.
If you opt for the bootstrap.memory_lock: true approach,you also need to define the memlock: true ulimit in theDocker Daemon,or explicitly set for the container as shown in the sample compose file.When using docker run, you can specify:
The image exposesTCP ports 9200 and 9300. For production clusters, randomizing thepublished ports with --publish-all is recommended,unless you are pinning one container per host.
By default, Elasticsearch automatically sizes JVM heap based on a nodes’sroles and the total memory available to the node’s container. Werecommend this default sizing for most production environments. If needed, youcan override default sizing by manually setting JVM heap size.
To manually set the heap size in production, bind mount a JVMoptions file under /usr/share/elasticsearch/config/jvm.options.d thatincludes your desired heap size settings.
For testing, you can also manually set the heap size using the ES_JAVA_OPTSenvironment variable. For example, to use 16GB, specify -eES_JAVA_OPTS='-Xms16g -Xmx16g' with docker run. The ES_JAVA_OPTS variableoverrides all other JVM options. The ES_JAVA_OPTS variable overrides all otherJVM options. We do not recommend using ES_JAVA_OPTS in production. Thedocker-compose.yml file above sets the heap size to 512MB.
Pin your deployments to a specific version of the Elasticsearch Docker image. Forexample docker.elastic.co/elasticsearch/elasticsearch:7.12.0.
You should use a volume bound on /usr/share/elasticsearch/data for the following reasons:
- The data of your Elasticsearch node won’t be lost if the container is killed
- Elasticsearch is I/O sensitive and the Docker storage driver is not ideal for fast I/O
- It allows the use of advancedDocker volume plugins
If you are using the devicemapper storage driver, do not use the default loop-lvm mode.Configure docker-engine to usedirect-lvm.
Consider centralizing your logs by using a differentlogging driver. Alsonote that the default json-file logging driver is not ideally suited forproduction use.
When you run in Docker, the Elasticsearch configuration files are loaded from/usr/share/elasticsearch/config/.
To use custom configuration files, you bind-mount the filesover the configuration files in the image.
You can set individual Elasticsearch configuration parameters using Docker environment variables.The sample compose file and thesingle-node example use this method.
To use the contents of a file to set an environment variable, suffix the environmentvariable name with _FILE. This is useful for passing secrets such as passwords to Elasticsearchwithout specifying them directly.
For example, to set the Elasticsearch bootstrap password from a file, you can bind mount thefile and set the ELASTIC_PASSWORD_FILE environment variable to the mount location.If you mount the password file to /run/secrets/bootstrapPassword.txt, specify:
You can also override the default command for the image to pass Elasticsearch configurationparameters as command line options. For example:
Install Macos In Docker
While bind-mounting your configuration files is usually the preferred method in production,you can also create a custom Docker imagethat contains your configuration.
Create custom config files and bind-mount them over the corresponding files in the Docker image.For example, to bind-mount custom_elasticsearch.yml with docker run, specify:
The container runs Elasticsearch as user elasticsearch usinguid:gid 1000:0. Bind mounted host directories and files must be accessible by this user,and the data and log directories must be writable by this user.
By default, Elasticsearch will auto-generate a keystore file for secure settings. Thisfile is obfuscated but not encrypted. If you want to encrypt yoursecure settings with a password, you must use theelasticsearch-keystore utility to create a password-protected keystore andbind-mount it to the container as/usr/share/elasticsearch/config/elasticsearch.keystore. In order to providethe Docker container with the password at startup, set the Docker environmentvalue KEYSTORE_PASSWORD to the value of your password. For example, a dockerrun command might have the following options:
In some environments, it might make more sense to prepare a custom image that containsyour configuration. A Dockerfile to achieve this might be as simple as:
You could then build and run the image with:
Some plugins require additional security permissions.You must explicitly accept them either by:
- Attaching a
ttywhen you run the Docker image and allowing the permissions when prompted. - Inspecting the security permissions and accepting them (if appropriate) by adding the
--batchflag to the plugin install command.
See Plugin managementfor more information.
You now have a test Elasticsearch environment set up. Before you startserious development or go into production with Elasticsearch, you must do some additionalsetup:
Mac Docker Install Ubuntu
- Learn how to configure Elasticsearch.
- Configure important Elasticsearch settings.
- Configure important system settings.
Mac Docker Install Kubernetes
Macos Docker Install
Most Popular
